DISC has implemented ISO 27001 for several organizations to achieve certification which includes but not limited to fortune 500 organizations.
DISC performs a security review (ISO 27k gap assessment) to identify and analyze risks and weaknesses in the security posture of
your organization and due diligence is achieved by virtue of ISO compliance. A gap assessment is performed utilizing international standard ISO 27002 2022 (Code of
Practice), ISO 27001 2022 (ISMS Specification) and company security policy, the purpose of the gap assessment is to evaluate the information security posture of your
organization.
ISO 27002:2022 has three control types, #Preventive, #Corrective and #Detective. Some of these controls share more than one control types. There are total 12 Detective, 13 Corrective, and 83 Preventive controls and 15 controls (12+13+83 = 108 -15 = 93) which share more than one control type in ISO 27002:2022 latest guidance.
There are 93 controls in Annex A, covering the breadth of information security management, including such areas as
Being certified with ISO 27001 can bring numerous advantages to an organization:
- Minimizes the risk of cyber-attacks on your company.
- Facilitates the demonstration of compliance with various regulations and standards.
- Lowers operational expenses by implementing only necessary controls.
- Prevents damage to reputation and financial penalties.
- Enhances customer retention through a compelling security narrative.
- Attracts new business opportunities by confidently addressing security concerns.
- Streamlines the process of completing security questionnaires, freeing up valuable time.
- Cultivates a stronger security culture and awareness within the organization.
- Reduces Cyber Liability Premiums by potentially over 200%
|
|
|
|
|
|
|
|
ISO 27001 helps you identify and manage risks
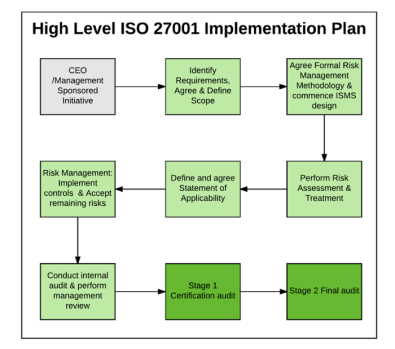
An ISMS is based on the outcomes of a risk assessment, which means the business needs to produce a set of controls based on the identified risks in order to minimise those risks. The risk assessment is conducted across the organization. It includes all the possible risks that the information can be exposed to, balanced against the likelihood of these risks materialising and the potential impact of such risks. Once the risk assessment has been conducted, the company needs to decide how it will manage and mitigate those risks. The business then needs to make a decision about how to decrease the risks based on allocated resources and budget.
Simplified ISO 27001 Certification
Continued Management all for a Fixed Monthly Fee
Reach compliance at your own pace - Dedicated ISO 27001 expertise to ensure you have the answers, guided documentation and extended team members you need when you need them.
Stay on target - DISC hosts weekly status/coordination/working meetings between your project team and our ISO 27001 experts dedicated to your project.
Save time and money - Leveraging our expertise, proven processes and artifacts simplifies the process of achieving certification.
Ensure you meet ISO 27001 requirements - DISC ensures your success by validating all artifacts to guarantee they fully conform to the standard.
Ensure 27001 is Operationalized (not just implemented) - DISC helps build the ISMS committee and chair committee meetings.
Ensure you are ready for your certification audit - DISC conducts your ISMS Internal Audit (including Corrective Action Plans & Management Review).
Support You Through the Audit -DISC provides on-site support to ensure your certification audit goes off without a hitch. We have a 100% success rate bringing clients to ISO 27001 certification.
Support You Post Certification - DISC provides the ongoing operational support to ensure that you successfully maintain your certification year after year.
Call or email to schedule an appointment
707-998-5164 info@DeuraInfoSec.com Continued
An ISO 27001:2022 certificate is a must-have. In some other cases, customers will recognize your dedication to excellence in providing high levels of security protection in your SaaS solutions by being ISO 27001:2022 certified. Whatever the situation, even with the cost of the implementation, ISO 27001 brings many benefits to your business. Benefits for SaaS organization.
- Fulfillment of Service Levels – The risk management approach of ISO 27001 can help a SaaS provider to decrease the number and impact of most common incidentsthat can decrease the level of service and/or website uptime, and to monitor service performance, increasing the chances that it will be capable of delivering the expected results at all times.
- Continuity of services – Sometimes incidents prove themselves far more critical to a SaaS provider than it can normally handle, causing a complete disruption of activities, and ISO 27001 can provide business continuity capabilities to ensure that the minimum agreed service levels will be maintained, or will be recovered quickly, and that the return to normal operations will be as quick as possible.
- Data ownership and control – For customers, just asimportant as having a SaaS provider to protect their information is the understanding that they, as customers, are still in control of their own information. ISO 27001 can provide a basis for establishing access control functionalities that can be used by the customers themselves to decide who can access their information, and thereby provide better assurance about the data integrity.
- Global compliance – SaaS providers have all the world as potential customers, and ISO 27001 can help them identify laws, regulations, and other information-related legal requirements that must be fulfilled for each country they want to have business in, decreasing risks not only to themselves, but to their customers, too.
- Proof of excellence on information protection – So, you’ve set your organization, processes, roles, and responsibilities, and you are achieving excellent results by protecting information. You are also aware that potential customers are looking for best-in-class service, and you have to show them that you are worth their investment. Before they get to know you better, with an ISO 27001 certificate you give them a globally recognized guarantee that they can rely on, until you start delivering evidence of your efficiency once they start using your services.
Hey I'm the digital assistance of DISCInfoSec for ISO 27k implementation.
I will try to answer your question. If I don't know the answer, I will connect you with one my support agents.
Please click the link below to type your query regarding ISO 27001 (ISMS) implementation
Benefits of ISO 27001 framework:
|
* Safeguard your valuable data and intellectual property * The framework addresses the security issues for the whole organization * Avoid penalties and losses due to data breaches |
| * Address compliance with various standards and regulations like (HIPAA, PCI, GDPR) |
| * Reduce the total cost of security by decreasing the total number of controls |
| * Perception of your business that you are serious about the security |
| * Enhance partners and vendors confidence |
| * The future deciding factor for international partners |
| * Obtain an advantage over your competitors |
Download ISO27000 family of information security standards today!
ISO 27001 Do It Yourself Package (Download)
ISO 27001 Training Courses - Browse the ISO 27001 training
courses
It is important to not only assess the control for completeness (all relevant areas are addressed) and comprehensiveness (each individual area is covered completely), but also this balanced framework
serves as the basis for both measuring an organization's effectiveness in addressing risk and structuring an organization's overall security program. Because ISO 27002 requirements are largely a
superset of other major regulations, achieving ISO 27002 compliance positions most organizations to be well on their way to meeting the requirements of PCI, SOX, SOC2 HIPAA and GLBA.
To achieve ISO compliance, thorough assessment utilizing all 93 controls will provide mitigating solution guidelines for gaps. Depending on your needs, size of your organization, availability of
key resources and information the final report can be produced within couple of weeks. Also depending on your requirement DISC may provide implementation guidance and metrics for all control
categories. To give your business an edge, contact us if you would like to compare your security practices with international standard.
The result of the assessment will not only establish and maintain security policy, but also validate policy's completeness, design new controls and provide a road map to mitigate risks and
to achieve certification. An assessment of risks will determine what issues need to be addressed and provide a guideline to meet security regulations and a road map to build a world class ISMS
(Information Security Management System). Controls are not only technological solutions but also cover people and organizational processes.
IBITGQ Lead Implementer
ISO 27002 assessment for as-is security posture
Build ISMS (ISO 27001) for to-be security posture
- ISO 27001 Gap Assessment based on Specification & Annex A
- ISO 27001 Implementation including ISMS policies & procedures
- ISO 27001 Risk Assessment Methodology based on ISO 27005
- ISO 27001 Risk Assessment of critical assets within the scope
- ISO 27001 Internal Audit
- ISO 27001 Awareness & Training
ISO/IEC 27002 the code of practice for information security management previously known as BS 7799-1 and then ISO/IEC 17799 [Press release on change of name]
ISO 27002 2013 (Code of Practice), ISO 27001 2013 (ISMS Specification) - Published Date September 2013
DISC offers a comprehensive ISO assessment to analyze the security posture of an organization. In the final report each control is defined and color coded using the base definition found in CMMI
(Capability Maturity Model Integration). This is a proprietary evaluation program. Contact us for a quote.
DISC is an approved associate consultancy of NQA Registrar
CMMI to ISO 27002
| Rating | CMMI level | ISO 27002 level | |
| 0 | Non existent | Complete lack of recognizable control | |
| 1 | Initial | There is an evidence that security issue exist and needs to be addressed, however no control exist to tackle the issue | |
| 2 | Repeatable | Security control is still in development with limited documentation | |
| 3 | Defined | Security control has been documented and communicated through training, but it is left to individual to follow control | |
| 4 | Managed | It is possible to monitor and measure security control compliance but management of the control is not fully automated | |
| 5 | Optimized | Security control has been refined to a level of ISO code of practice, based on result of continuous improvement |