“De-Perimeterized model” means protecting assets regardless where they live. Visibilities into your endpoints outside your perimeter improve security posture and compliance.
DISC performs Cloud Security Assessment to assess your compliance, security and privacy requirements to limit your risk exposure in the cloud.
Contact us to explore our services
How Can Organizations Reduce Their Cloud Security Risks?
According to study by McAfee, only 69% of businesses trust the public could to keep their data secure in the cloud. But cloud use is increasing. So based on this study, 31% of businesses are not keeping their data secure, this number may be higher for small to medium size (SMB) organizations. With all the standards and compliance regulation which may apply to your organization, your organization may be liable to civil and criminal liabilities for negligence to build a security program based on these standards and regulation which apply to your organization.
Cloud service provider (CSP) is a third party to your organization, how do you integrate the third-party risk management (TPRM) into your overall information security and risk management program?
Smaller companies are particularly vulnerable to risks with cloud providers. Because of their size, they may use cloud services for services for sensitive data that larger companies might have on-prem. They may not have security program in place to fund information security to have security professional on staff to deal with cloud security as well as on premise data security.
TPRM approach to Cloud Services
1. What is Cloud?
Cloud is about Platform-as-a-Service (PaaS), Software-as-a-Service (SaaS), or Infrastructure-as-a-Service (IaaS). These models are very different, and come with different security accountability and responsibilities for your organization and cloud providers.
- Many people are referring to "Cloud" in only the most vague and unspecific terms. Also there is no "The Cloud” there are different cloud product offerings by Amazon, Google, Microsoft and one would have to answer the questions for each of these separately.
- Cloud computing is very specifically a variable resource capability where the number of machines expands and contracts with demand, more or less automatically. How it does this and all the other factors also depend on service contracts with the vendor which can affect security of infrastructure and data.
- Cloud API's also afford massively parallel computing and so tasks move from physical machine to physical machine with the expansion and contraction.
2. Every Cloud Service Provider (CSP) is unique
Enterprise level organizations have advanced and complex security controls in place, compare to small organization. AWS as a CSP has advance and mature set of infrastructure security controls in place compare to small cloud vendor. The key is, understanding your accountability as an organization, that you own your data and responsible for its security.
3. Cloud service vendor
Your CSP may be using multiple vendors to provide the services based on your contract. These cloud service vendor should be considered as a dependencies of CSP, and should be included in the third party risk management to assess overall risk (of privacy and security) to your organization
4. TPRM program
Most organizations need to know their information is safe with their third party cloud provider as well as prove to their key stakeholders, privacy and security of their data. DISC Security designs and executes TPRM program to help organizations understand and mitigate third party risks.
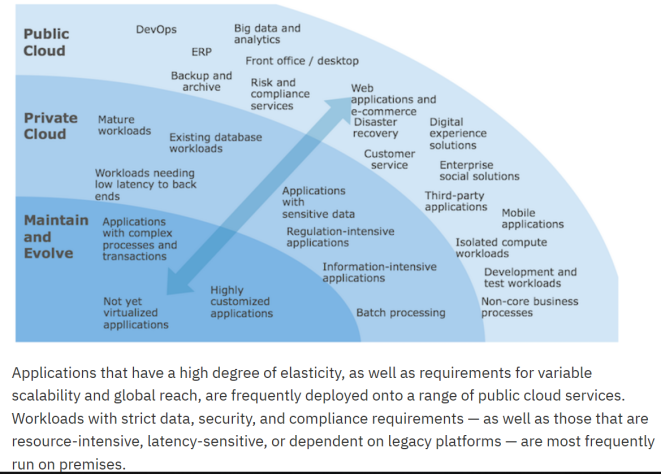
5. Applications in the cloud
How to protect your data in the cloud
Develop TPRM program and integrate it with your information security program
97% of organizations use CSPs. Every organization has third-party risks. TPRM program will help you manage those third-party risks
Which cloud services?
According to the McAfee study, the average company uses 25 different CSPs. Most organizations don’t understand all the cloud services they are actually using. TPRM program will not only assist you knowing all these vendors (asset register) and their services, will also assist you with prioritize and manage those risks.
Relationships with your cloud service providers
Building a relationship with your CSP and reviewing their contract on regular basis is a key to understand your accountability and responsibilities of protecting your organization and customer data.
Shadow IT
“Shadow IT” includes those IT services that are driven and managed outside of the traditional IT infrastructure. Shadow IT should be addressed in Cloud Security Policy. Cloud Access Security Broker (CASB) solution can assist your organization to discover Shadow IT.
Security Strategy
Perform a cloud security assessment based on frameworks such as ISO 27001/17/18, SOGP or NIST CSF and build your security strategy.
Cloud Security Principles
Details and context for the 14 Cloud Security Principles, including their goals and technical implementation
For each of the 14 principles, we answer three questions:
- What is the principle? A description giving the principle some context
- What are the goals of the principle? Concrete objectives for the implementation to achieve
- How is the principle implemented? Details for a set of possible implementations
User data transiting networks should be adequately protected against tampering and eavesdropping.
2. Asset protection and resilience
User data, and the assets storing or processing it, should be protected against physical tampering, loss, damage or seizure.
A malicious or compromised user of the service should not be able to affect the service or data of another.
The service provider should have a security governance framework which coordinates and directs its management of the service and information within it. Any technical controls deployed outside of this framework will be fundamentally undermined.
The service needs to be operated and managed securely in order to impede, detect or prevent attacks. Good operational security should not require complex, bureaucratic, time consuming or expensive processes.
Where service provider personnel have access to your data and systems you need a high degree of confidence in their trustworthiness. Thorough screening, supported by adequate training, reduces the likelihood of accidental or malicious compromise by service provider personnel.
Services should be designed and developed to identify and mitigate threats to their security. Those which aren’t may be vulnerable to security issues which could compromise your data, cause loss of service or enable other malicious activity.
The service provider should ensure that its supply chain satisfactorily supports all of the security principles which the service claims to implement.
Your provider should make the tools available for you to securely manage your use of their service. Management interfaces and procedures are a vital part of the security barrier, preventing unauthorized access and alteration of your resources, applications and data.
10. Identity and authentication
All access to service interfaces should be constrained to authenticated and authorized individuals.
11. External interface protection
All external or less trusted interfaces of the service should be identified and appropriately defended.
12. Secure service administration
Systems used for administration of a cloud service will have highly privileged access to that service. Their compromise would have significant impact, including the means to bypass security controls and steal or manipulate large volumes of data.
13. Audit information for users
You should be provided with the audit records needed to monitor access to your service and the data held within it. The type of audit information available to you will have a direct impact on your ability to detect and respond to inappropriate or malicious activity within reasonable timescales.
The security of cloud services and the data held within them can be undermined if you use the service poorly. Consequently, you will have certain responsibilities when using the service in order for your data to be adequately protected.
Cloud Security Assessments